Publishings Digital Youth
Program Areas
-
Media Advisory – Save the Date FOR IMMEDIATE RELEASE October 3, 2018 Contact: Jeff Chester jeff@democraticmedia.org (link sends e-mail) COPPA--Protecting Children’s Privacy Online for 20 Years Sen. Ed Markey, Advocates and Experts Celebrate COPPA as they focus on future challenges posed by the digital marketplace October 17th, Capitol Hill, Open to Public Washington, D.C. To mark the 20th anniversary of the 1998 Children’s Online Privacy Protection Act (COPPA), Senator Edward J. Markey (DMA) —its principal congressional sponsor—will be joined by key representatives from the consumer, child advocacy, and privacy groups involved in implementing the law, at a public forum on Wednesday, October 17 from 12:30-3:30 pm in Room 385 of the Senate Russell Office Building (SR-385). Senator Markey will deliver a keynote speech followed by two panels featuring representatives from Electronic Privacy Information Center, Campaign for Commercial Free Childhood, Common Sense Media, Center for Digital Democracy, Color of Change, and Institute for Public Representation (Georgetown University Law Center), among others. Prof. Kathryn C. Montgomery, who spearheaded the public campaign that led to COPPA, will moderate. “COPPA is the nation’s constitution for children’s communication. For 20 years it has shielded our nation’s children from invasive practices and encroaching actors on the internet,” Sen. Markey noted. “It puts children and families in control and holds violators accountable when they compromise kids’ privacy. As we celebrate the 20th anniversary of COPPA, we must look to the future.” In addition to discussing COPPA’s impact, speakers will explore the expanding interactive and data-driven world young people face today, which is being transformed by a host of powerful technologies, such as artificial intelligence, virtual reality, and internet-connected toys. “In 2018, children grow up in an increasingly connected and digital world with ever-emerging threats to their sensitive personal information,” explained Sen. Markey. “Two decades after the passage of this bedrock law, it is time to redouble our efforts and safeguard the precious privacy of our youngest Americans.” The event is free and open to the public, but seating is limited. Lunch will be served. Please RSVP to jeff@democraticmedia.org (link sends e-mail).
-
The Center for Digital Democracy (CDD), Berkeley Media Studies Group, and Color of Change urge the Federal Trade Commission (FTC) to specifically acknowledge the important issues involving the privacy and welfare of young people by adding this issue to its proposed hearing agenda on competition and consumer welfare.
-
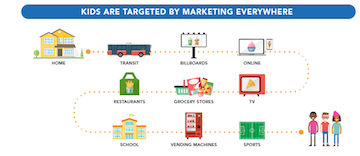
Around the world citizens (link is external) and governments (link is external) are putting efforts toward limiting the marketing of unhealthy foods to children in order to address the growing obesity (link is external) epidemic worldwide. In the US, Congress and the Federal Trade Commission rely on weak self-regulatory industry standards, but under Canadian Prime Minister Justin Trudeau, the government of Canada wishes to see restrictions placed on the marketing of food and beverages to children. This was a goal written directly into the Health Minister's mandate letter (link is external) signed by Trudeau in October 2017. As a result, Health Canada, the department of the Canadian government with responsibility for national public health, is considering new regulations that would impose broader restrictions on food advertising that is targeted at those under 17. It could cover everything from TV, online and print advertising to product labelling, in-store displays and even end some sponsorships for sports teams. Health Canada's consultations (link is external) on how it should approach restricting advertising of "unhealthy food and beverages" to kids began in June of 2017 and concluded in early August last year. Although a few contributors opposed any attempt to restrict marketing to children, the summary report (link is external) states that "Overall, the proposed approach and supporting evidence for restricting marketing of unhealthy food and beverages to children were well received." The authors of the report point out that the "issue of age was not an area of inquiry," but most contributors supported the idea of including children between 13 and 17 years of age. Aiming to define "unhealthy foods," the consultation proposed to focus on restricting certain nutrients of concern (sodium, sugars, and saturated fats), and most commentators supported setting the stricter threshold option (of 5% ) for the proposed restrictions, which were based on a percentage of daily values (% DV). Commentators strongly preferred that option over the weaker proposal (15% DV). Using the percentage of daily values to define which foods are "healthy" or "unhealthy" relies on the already existing mandatory food labelling for most relevant foods. In addition to the proposal to restrict certain nutrients of concern, the proposed restrictions to the marketing of non-sugar sweeteners to children was also positively received. For the consultation, Health Canada looked at the Quebec ban (link is external) on advertising to children, which has been in place since 1980, and covers any advertising, not just food-related advertising. In that province, companies cannot market unhealthy food to children under 13 years old. Quebec has the lowest obesity rate (link is external) in Canada among children aged six to 11 and the highest rate of fruit and vegetable consumption. The Stop Marketing to Kids Coalition (link is external) (M2K Coalition), which includes the Heart and Stroke Foundation of Canada, the Childhood Obesity Foundation, the Canadian Cancer Society, Diabetes Canada, Dietitians of Canada, and the Quebec Coalition on Weight-Related Problems, supports the so-called Ottawa Principles (link is external). These evidence-based, expert-informed and collaboratively arrived principles call on governments to restrict the commercial marketing of all food and beverages to children and youth age 16 years and younger. Restrictions would include all forms of marketing with the exception of non-commercial marketing for public education. The M2K Coalition has taken this stance because of the complexities associated with defining healthy versus unhealthy food. The ad industry in Canada has some self-regulatory restrictions in place under the Canadian Children's Food and Beverage Advertising Initiative (link is external). That program, in which many major food companies are participants, sets out nutrition criteria for products that can be advertised in environments where kids under 12 make up 35 percent or more of the audience. The Association of Canadian Advertisers has criticized Health Canada's proposal as "significantly overbroad," calling it an "outright ban on most food and beverage marketing in Canada." The Canadian advertising initiative has tightened its criteria over time and is now monitoring online advertising more closely. 2016 was the first full year in which participating companies that advertise to kids had to ensure their products met new, tighter limits (link is external) on calories, sugar, sodium and saturated and trans fats. However, in 2017, a study (link is external) from the Heart and Stroke Foundation of Canada called into question how effective this effort has been. It looked at the most popular websites visited by children and teens, and found ads for products high in sugar, salt or fat. During the time that the Canadian government began to explore the right approach to restricting the marketing of unhealthy foods to children, Senator Nancy Greene-Raine introduced a private members bill in the Senate in the fall of 2016, seeking to amend the Food and Drugs Act to prohibit the marketing of unhealthy foods and beverages to children (Bill S-228). This would put the activities of Health Canada on a legal basis. The Senator amended the bill to reflect the federal government’s proposed approach on raising the age limit to age 16 and under and kept the focus on “unhealthy” food and beverages. Bill S-228, The Child Health Protection Act (link is external), unanimously passed the Senate in September 2017. Two amendments to the bill were introduced during the first hour of debate in the House of Commons in December 2017, which included a reduction in the age of protection to under 13 (from 17) years, and the introduction of a 5-year post-legislation review period. The rationale for the change in the age amendment was to make the bill more likely to withstand a court challenge, given that the Quebec legislation restricting marketing to children under 13 years withstood a legal challenge in the case of Irwin Toy v Quebec (1989). In this case, the Supreme Court of Canada allowed limits on commercial advertising to children under 13 as constitutionally valid. The Court confirmed that "...advertising directed at young children is per se manipulative." (link is external) And so, while the Court found that the restrictions violated the freedom of expression under the Charter of Rights and Freedoms, a majority of the Court considered this violation to be a justifiable limitation necessary to protect children. For now, the bill is working its way through Parliament. Hopefully, the food industry will not further water down the requirements of the bill. If all goes well, our neighbor to the north will have a law in place by September 2018 that will advance public health and put children's health above the profits of the food industry. --- See attached infographic.
-
Press Release
Statement of Jeff Chester on plans by FCC to review 3-hour Children’s Educational TV Programming Rule
Broadcasters want to kill one of their only few public interest obligations: to air at least 3 hours of educational children’s programming a week. The FCC is engaged in another outrageous form of digital highway robbery—to steal from kids in order to allow TV giants to make even more profits from shows filled with commercials. Broadcasters now earn billions of dollars from their free public license to transit television—including getting access to invaluable cable TV channels. They are supposed to serve as a “Trustee” of the airwaves—not video programming bandits. Without their 3 hour kidvid requirement, broadcasters will able to reap the financial rewards without any real payback to the public. Millions of kids in the U.S. live in homes that can’t afford cable or broadband. Kidvid programming plays an important role providing access to some quality content for these children. The Pai FCC—as it’s done by killing network neutrality—is engaged in a slash and burn campaign when it comes to much needed public interest consumer protections for media. We will vigorously fight this cynical and harmful move by the FCC to place the interests of the TV lobby ahead of America’s children. CDD helped lobby in the 3-hour rule in the 1990s and plans to work with allies, such as Sen Ed Markey, to protect the interests of parents and children. -
Press Release
Death of Net Neutrality Will Spur Greater Loss of Digital Privacy, Further Content Consolidation & Control
Statement of Jeff Chester, CDD
The phone and cable lobby will use its new power over the Internet to further erode the privacy rights of Americans. Comcast, AT&T, and Verizon will be entirely free to tap into the data flowing from our mobile devices, PCs, gaming and streaming platforms and set-top boxes. These ISP giants have already built up a formidable (link is external) commercial data gathering and Big Data analytics infrastructure. Now they will expand their gathering of our personal information, inc. financial, health, media use, and also force competitors to share the data they collect. If you want ISPs to give you preferential treatment, content providers will be forced to give up your data, so phone and cable can further expand their ad revenues. Independent and small content companies—including non-commercial and diversely-owned services—will be pressed to consent to terms that favor the digital gatekeepers that control our broadband highway. The FCC’s Net Neutrality decision will trigger a powerful wave of consolidation and deal making that further reduces the range of content and services we should expect in the 21st Century (including for children). We also believe that Google, Facebook and other providers will likely make their peace with the big ISPs, creating a powerful alliance that controls the U.S.’s digital destiny. CDD will be a part of the collaborative work to address this. We urge everyone to also “follow the data” as they examine the digital marketing plans of Verizon, Comcast and AT&T (link is external). There they will find plenty of opportunity to educate the public about our digital future has been placed at great risk. -
Statement of Kathryn C Montgomery, Ph.D. Professor, School of Communication, American University Senior Consultant, Center for Digital Democracy December 4, 2017 In its first formal move to enter the children’s digital marketplace, Facebook has taken a responsible approach to this sensitive age group. It has created a “walled garden” messenger service designed exclusively for younger children; established strong parental controls; kept the service free of advertising; and restricted the use of many data collection and targeting practices that are employed routinely in its other services. The Children’s Online Privacy Protection Act (COPPA) – which we helped pass in 1998, and which was updated in 2012 – has established a strong framework for protecting children 12 and under from unfair data collection and targeting. However, additional safeguards are necessary to protect young people from powerful new forms of commercial surveillance in the Big Data and Internet-of-things era. By designing an ad-free and safe environment for children, Facebook is playing a leadership role in developing responsible corporate practices that could be the basis for industry-wide guidelines. But it is too early to understand fully how young people’s engagement with this new generation of digital interactive platforms will impact their psychosocial development. All stakeholders—including health professionals, educators, scholars, advocates, policymakers, and corporations — will need to monitor very closely how these services evolve. ---
-
Google + Ad Industry Study Shows Influencers on YouTube Sell Snacks, Toys, Alcohol
Illustrates Need for 21st Consumer Safeguards for Unfair/Deceptive Marketing
Sanjay Nazerali, Chief Strategist of Carat, a global media market leader in digital media, writes about how YouTube influencers are rewriting the marketing rulebook. Working in strategy at one of the world’s largest media agencies, I’ve witnessed countless pitches about influencer marketing and the growing power of creators. With engaged audiences in the millions and passionate fans hungry for content, YouTube creators are already an established channel for brands looking to run ads. In fact, Carat’s latest analysis suggests online video investment (including YouTube) can be increased by 3X compared to planned level. But increasingly, these influencers are also becoming attractive partners for deeper collaborations. Clients are initially enthusiastic, assuming this is the digital age’s answer to celebrity marketing and endorsement. Then the thorny business questions arise, such as: So what’s it actually doing for my brand? Do I do an endorsement or product placement—or what? Isn’t it just for millennials, beauty brands, and makeup tutorials? These have always been tough questions to answer. Even though almost everyone has been jumping on the influencer bandwagon, few understand what “influence” really is or how it works. Until now. Celebrity marketing and influencer marketing offer fundamentally different benefits for brands. Together with YouTube and Nielsen, my team analyzed the results of hundreds of brand and creator videos in the U.S. and the U.K to understand the impact of influencers for brands. It’s a critical first step in establishing a business-led rulebook for this new world—and it’s already changing how I approach my own plans. 1. Influencers are not the same as celebrities Influencers, however vast their reach, are absolutely not “today’s celebrities,” and celebrity marketing and influencer marketing offer fundamentally different benefits for brands. For instance, we found that celebrities are more effective at driving recall than creators (84% versus 73%). Given that a celebrity’s job is to be famous and memorable, that makes sense. Where YouTube creators really start to gain the upper hand is in deeper brand involvement. Brand familiarity is a good example. If we want to get an audience to really understand us, our work, our values, or our products, then collaborations with YouTube creators are 4X more effective at driving lift in brand familiarity than those with celebrities. When it comes to purchase intent, it’s an even match: our research found that influencers were just as likely as celebrities to drive buying decisions. Influencer marketing appears to play a fundamentally more pragmatic role. Why? My hunch is that it’s because fans feel very connected to the YouTubers they love. The best creators have formed authentic bonds with their fans, which means fans trust what they have to say, and turn to them for brand and product recommendations. 2. It’s not just a ‘beauty’ thing Beauty brands were one of the first to team up with influencers, and creators have established a huge presence among the YouTube beauty community. About 86% of the top 200 beauty videos on YouTube were made by creators rather than professionals or brands. But what’s interesting about our findings is just how far influencers stretch beyond the beauty category. We tested nine additional categories, including auto, alcohol, snacks, and toys. Across all nine categories, working with influencers leads to lifts in brand metrics, from familiarity to affinity to recommendation. In some categories, such as snacks and alcohol, they can have even more impact, driving significantly higher than average purchase intent. So the idea that influencer marketing is purely for young people who are looking at fashion and beauty brands simply isn’t true. 3. The ‘how’ matters as much as the ‘who’ Celebrity marketing has historically focused on endorsement, sponsorship, and product placement. Influencer marketing has developed far more options, and it’s important to understand which of these work best—and for which marketing goals. Deep thematic integrations with creators stand out as driving the highest results for brands. These are more involved integrations where the influencer plays a role in creating a piece of content – such as a demo – with the brand. It’s far deeper than product placement and it works more effectively. While there were many consistencies across categories, we also saw some nuances, which are important for clients to understand. We found that simpler brand integrations, like a product endorsement or just featuring a creator in an ad, also showed positive results for brand affinity in all categories tested. Of course, deep collaborations can be more than some brands are ready for. For some objectives and categories, simply running their own ads on YouTube creator content will still be the easiest and most effective way to tap into the power of these influencers. 4. Don’t lose sight of why people love YouTubers We often assume that the right influencer is either an aspirational version of our target audience or that they’re just like celebrities. Neither of these assumptions is correct, and it’s perhaps here that celebrity and influencer marketing differ the most. Whereas celebrities need to be trendy and stylish, consumers expect creators to be friendly, funny, and, yes, sometimes irreverent. Irreverence is interesting, because it drives credibility. Irreverence strongly suggests independence, and it’s this that builds trust. It can also be incredibly valuable for brands. If a creator usually ridicules things they don’t like, you can be sure that when they praise something, they mean it. Humour is also interesting, because it reflects a sense of community. YouTube helps forge a special relationship between followers and influencers, one that reflects a sense of co-ownership. This familiarity creates a degree of intimacy that makes the use of humour seem much more natural than it would do with celebrities. This is probably also why we see celebrities, such as Dwayne Johnson, increase their influencer scores when they get really active on YouTube. Prioritization and strength of attributes by gen X and gen Y associated with celebrities are different to creators. --- For the full article, visit http://bit.ly/2z6MHng (link is external) Is it Hype? Or is it Real? Decoding the Influence of YouTube Influencers Read more at http://newyork.advertisingweek.com/CALENDAR/-google-seminar-2017-09-26-1... (link is external) -
Press Release
Advocates Call on FCC to Protect Programming and Advertising Safeguards for Children's TV
Commission Must Reject TV Industry Proposal to Undermine Public Interest Obligations
WASHINGTON, D.C. – Advocates called today on the Federal Communications Commission (FCC) to reject an effort by major media companies to eliminate or weaken important rules for children’s television. The National Association of Broadcasters, Internet and Television Association (NCTA), CBS, Disney, Fox, Univision, and others have asked the FCC to significantly reduce advertising limits on children’s programming. Industry commenters also urged the FCC to reconsider rules that require broadcasters to provide quality educational programming as part of their obligation to serve the public interest. In comments filed today, Campaign for a Commercial-Free Childhood and the Center for Digital Democracy called on the FCC to reject industry proposals to repeal or modify the current rules. “The Trump Administration and the FCC should stand up for the rights of children and parents and reject this crass campaign by the broadcast lobby,” said Jeff Chester, executive director of the Center for Digital Democracy. “The broadcast industry receives billions of dollars in benefits from its free use of public resources, including invaluable rights to the airwaves. It is unconscionable that TV stations and networks want to kill off one of their few remaining obligations to the public.” In April, the FCC issued a public notice on its “Modernization of Media Regulation Initiative,” asking for suggestions about which of the FCC’s media-related rules should be modified or repealed. Media companies replied with a deregulation wish list that would allow them to use kids’ television programming to market directly to children. The major networks urged the FCC to relax its rules prohibiting product integration and product placement on kids’ shows, arguing that YouTube and other child-directed online services are not subject to those restrictions. Advocates responded by pointing out that internet and mobile providers are simply ignoring longstanding children’s media principles, which are based on child development, and that a lack of online regulation is not a good reason for the FCC to eliminate important safeguards for the millions of children who watch traditional TV. “It is extremely disappointing that broadcasters want to join the race to the bottom when it comes to exploiting children’s developmental vulnerabilities for profit,” said Josh Golin, executive director of the Campaign for a Commercial-Free Childhood. “Media companies want to gut longstanding safeguards because young people an incredibly lucrative market for advertisers. But research demonstrates that children are particularly vulnerable to marketing and benefit from rules that require ad limits and separation of programming and commercial content.” Advocates also oppose a request by the Internet and Television Association to repeal an FCC rule known as the “website display rule.” The FCC adopted this rule in 2004 to prohibit advertisers from engaging in “host-selling” to children, which the transition to digital broadcasting could otherwise allow. Angela J. Campbell, director of the Institute for Public Representation at Georgetown and counsel to some of the advocates, called the effort to repeal this rule disingenuous. “The media companies say the website display rule is unnecessary because television has rarely been used to interact and target advertising to children,” she said. “But at the same time, these companies engaging in a practice known as ‘programmatic marketing,’ which offers advertisers the ability to target ads to specific viewers of cable and broadcast television programming.” In addition, advocates oppose efforts by media companies to be relieved of their public interest obligation to provide educational programming for children, and to produce public reports to help the FCC determine whether that programming meets the obligations laid out in the Children’s Television Act. “The television industry made a commitment to serve the nation’s children by providing quality educational programs,” explained Professor Kathryn Montgomery of American University, who led the effort to strengthen the FCC’s rules on the Children’s Television Act. “However, broadcasters failed to live up to these minimal obligations and the FCC has been irresponsible in allowing the industry to evade one of its only remaining public interest requirements. Rather than considering elimination of these rules, the FCC (and Congress) should conduct an investigation into TV programming and advertising practices directed at children.” ---- The comments can be read via the attached PDF file below. -
FameBit is an online marketplace that connects YouTubers with brands that are interested in advertising their products and services. This provides creators an opportunity to earn money with their content by partnering with brands that are relevant to their audience. Learn about Famebit, the Self-Service Influencer Marketing Platform. For more information, visit https://famebit.com/brands (link is external)
-
The Center for Digital Democracy (CDD) and Campaign for a Commercial-Free Childhood (CCFC), by their attorneys, the Institute for Public Representation, respond to the Federal Trade Commission’s (FTC or the Commission) request for comment on proposed changes to TRUSTe’s COPPA Safe Harbor program. TRUSTe has sought approval of changes to its COPPA Safe Harbor program that it states are necessary to comply with an Assurance of Discontinuance it recently entered into with the New York Attorney General’s Office (NYAG). While the proposed changes themselves do not appear objectionable, the facts leading up to this proposal strongly suggest that TRUSTe has violated its 2015 Consent Decree with the FTC by misrepresenting its practices for assessing operators of child-directed online services (Operators). CDD and CCFC ask the FTC to conduct an investigation of TRUSTe to determine if it has in fact violated the Consent Decree, and if so, to take all available enforcement action against TRUSTe. Further, to protect the privacy of children pending the outcome of the investigation, they ask the FTC to suspend TRUSTe’s COPPA Safe Harbor program. (Link to the full report attached below.)